Project Encrypt
Project encrypt is an ongoing personal hobby of mine to fully encrypt every activity I do online. This post will cover almost everything I do to secure my privacy and data online.
I will go over everything in detail but the summary is that this project includes:
- Passkeys for passwordless login and 2FA.
- Email aliases for every account.
- Encrypting email, storage, calendar, passwords & more.
- Generating credit card number cvv’s for every purchase.
- Secure messaging & contact key verification.
- App permissions
- Emergency sheets & backups.
If you follow this project, or any individual steps, your online data will definitely be safer and more secure than before.
Passkeys, Security Keys & 2FA/MFA⌗
If you’re not aware of what passkeys are yet, then let this be the one important takeaway from this article.
Passkeys are a way to log in to your accounts without having to remember a password, and sometimes in the case of passwordless then you don’t even need to remember your username. The passkey is generated and stored securely on your device or inside your password manager and can’t be accessed easily without device access.
Passkeys are not only more secure but also more convenient than passwords because they can be accessed via biometrics (FaceID/TouchID) or a master password.
To start using them, navigate to the security settings for any product you use and check if they support them. This is what the Google security settings look like for passkey registration:
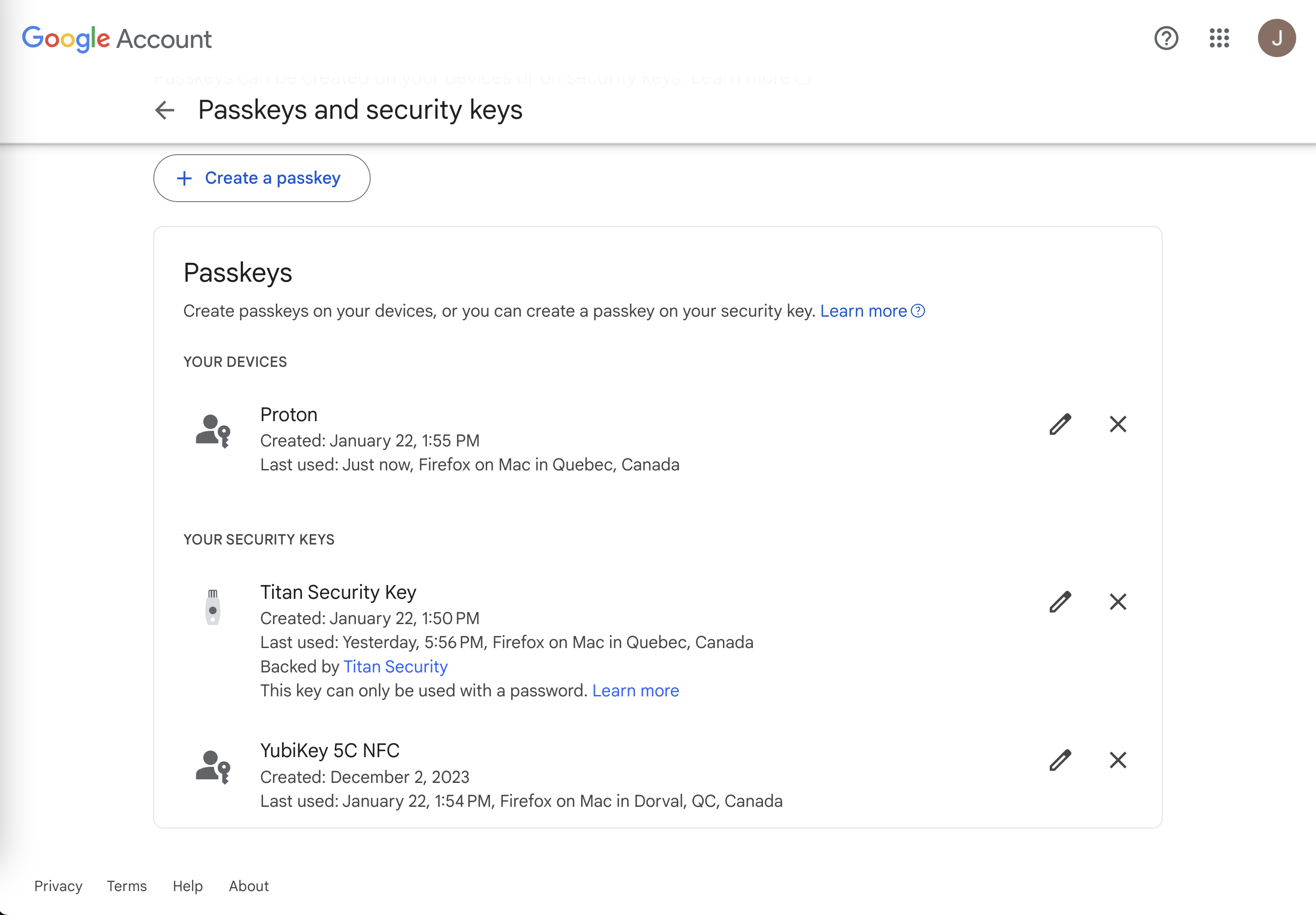
When registering a passkey, you can choose where to save it, either in a password manager or using a physical security key like a Yubi key.
For some more information on passkeys and security keys, here are some recommended links:
One other great advantage of passkeys is that they can be used for two-factor authentication (2FA), so not needing to copy/paste codes from an authenticator app or email/text message is a huge convenience with no security downside.
Not every product or service supports 2FA or passkeys, and the ones that do will support it to varying degrees. For example, some sites may have 2FA but only for text message codes and email codes (looking at you Banks and Government services…), which is less secure than things like an Authenticator app or passkeys.
Whenever creating a new account for any product or service, I always enable 2FA and register multiple devices. My preferences are (in order):
- Passkeys with physical security keys - (Yubi Key / Titan Key)
- Passkeys saved in a password manager
- Authenticator App
- Text Message / Phone Call
I usually register two security keys and one passkey in my password manager. Prefer to use passkeys if supported, if you’re in the Apple ecosystem then their built-in password manager has support for them already. Ditto for Android. If passkeys are still confusing, then opt to use an authenticator app (How authenticator apps work) like Ente for 2FA codes. The app shows codes rotating over time, and you must copy/paste them into the app during login.
Text message 2FA is by far the weakest form of 2FA, below is a good video about how easy it is for bad actors to intercept phone calls and text messages without you knowing it.
Email Aliases⌗
The idea of email aliases is to have a different email address for every online account.
This means having one email for something like Twitter and a different email for Instagram. There are many advantages to doing this, one benefit is spam management - if you start receiving spam to one email then you can just deactivate it.
It also allows you to centralize the forwarding process, so if one day you are forwarding all emails to a master address like name@domain.com and you would like to switch all your 150 accounts to a different address, then it’s as easy as switching in one place instead of inside all 150 accounts.
Apple supports aliases with their “Hide my email” feature in iCloud to generate email addresses easily or with “Sign in with Apple”.

I used Apple’s for a while and now use SimpleLogin for aliases.
Another benefit of aliases is that it keeps your master email unknown to anybody. This allows you to easily control who has access to contacting you. Nobody will know your real email, only your aliases, and you can easily deactivate an alias if someone uses it without permission.
Secure aliases like Apple’s or Proton’s are different than ones that services like Gmail provide with the
+trick. The+trick does not hide your original email, and anyone who knows that will have access to messaging you directly to your original email.
Encrypted email, storage, calendar & passwords.⌗
This section is dedicated to Proton - proton is a product suite that provides encryption for various tools and has replacements for things like email, storage (like Google Drive), calendars, VPN’s, wallets, and passwords, but all private and end-to-end encrypted (E2EE).
I have all my email aliases forwarded into my Proton mail account, I use Proton Storage for storing encrypted files, Proton Calendar for my calendar needs, and Proton Pass for my password manager which includes authenticator codes, passkeys, and email aliases. This suite replaces my need for similar Google products that are not encrypted.
If you’re interested in trying out Proton, I highly recommend it, and I have a referral code: https://pr.tn/ref/MQ4N9PEJTH10
If you would like to send me an E2EE email, please check out my contact page for my public PGP encryption key.
Credit Cards⌗
As often as possible I will use Apple Pay to pay with my credit card as Apple automatically generates new CVV’s with every purchase, masking your real CVV - this prevents vendors from stealing your full credit card information, as the generated number is only valid for that one time purchase.
Also, I use Wise to generate virtual prepaid credit cards when I really don’t trust the company I’m purchasing from. This protects my real CC number and if the prepaid card number is stolen then there will be no funds on it besides what I originally needed it for.
Messaging & Contact Key Verification⌗
Messaging with friends and family is usually done via iMessage, and sometimes with Signal when my contacts have it installed. Signal is a true end-to-end encrypted chat - it has no ads, no tracking and doesn’t gather metadata like other encrypted chats such as WhatsApp.
Preferably I would use Signal all the time, but not everyone understands the benefits yet - it is up to us to spread the word about Signal to friends who have not heard about it yet.
For iMessage I have enabled and set up Contact Key Verification with a few contacts to verify devices, this provides some extra security around account takeovers and you will be warned if a message is coming from an unverified device. But, it is a slow and manual process to verify each individual contact, and trying to explain to everyone the benefits of contact key verification is really difficult.
Details about Contact Key Verification from Apple Security Engineering
This is my public verification code:
APKTIDxRWrX5TLPlHGKpt7vDntZ832yLS0hNee8bVc3Fk0MDWjnw
iMessage is not perfect, but it seems to be the lesser of evils compared to services like WhatsApp, FB Messenger or Telegram which claim to be E2EE but are tracking a lot of extra metadata about you.
App Permissions⌗
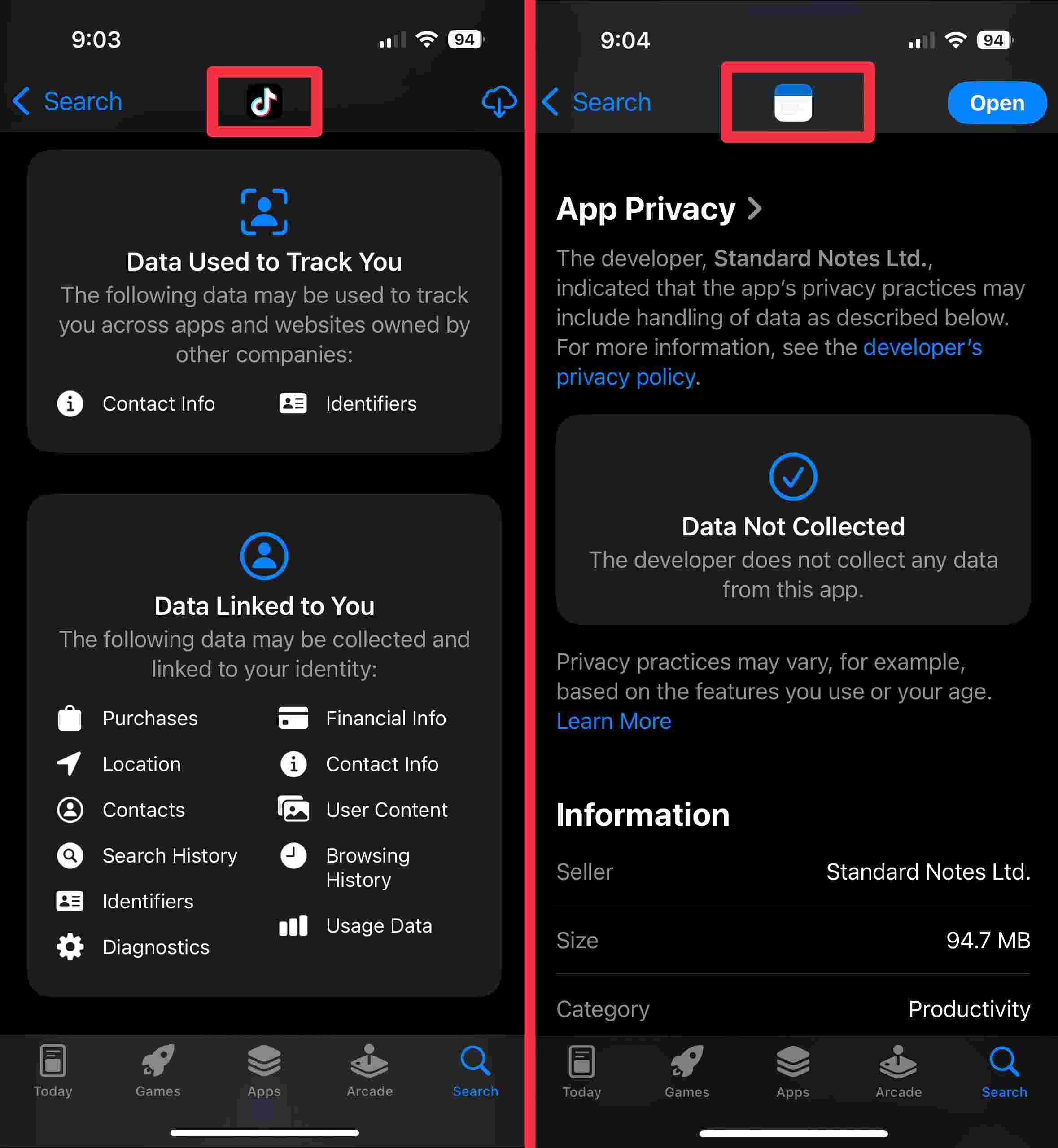
On the iPhone’s AppStore, there is a little known section at the bottom of every app that lists all the data the app has access to and links to you. I always try to avoid apps that grant themselves access to too much information.
Check out this comparison between what TikTok has access to, vs the Standard Notes app.
Emergency Sheet & Backups⌗
When using password managers, email aliases, and authenticator codes, it is important to have a solid strategy for doing periodic backups of this data because if you lose access to it one day, it will cause endless problems.
I have two methods of backups, and both are encrypted in different ways.
My primary backup method is using my personal server and database that I have hosted in an undisclosed data center. I have created a personal app that takes any data I want and encrypts it using a provided encryption key. The encrypted data is stored in my database and no encryption keys are stored with the server or database. This ensures that even if there’s a data breach, all the data would be encrypted without possibility to decrypt.
The second method is using Google Drive to store encrypted backups from Proton Pass. I store the encryption keys on my emergency sheet.
Finally, I created an emergency sheet. This is a physical paper sheet I keep in my house with master passwords, encryption keys, and recovery codes in case I lose access to anything very important. This is a worst-case scenario sheet, but it’s always good to have just in case.
Miscellaneous⌗
There are a lot of other small things I do that don’t warrant their own section so I’ll just list them here quickly:
- Turn on Advanced Data Protection for iCloud storage, which encrypts iCloud data, which is off by default. (Everybody should do this one, it’s easy and important)
- Turn off location services on iPhone.
- Reject any prompts for Data Tracking on apps.
- Use VPN’s as often as possible to mask IP addresses.
- Avoid products and services from Google and large tech companies.
- Avoid using or downloading apps such as TikTok, Facebook, Instagram or Twitter.
- Use DuckDuckGo instead of Google Search.
- Avoid any “always listening” smart-home products like Google Home, Amazon Alexa, or Siri.
- Use Firefox instead of Chrome.
- Use Standard Notes for note taking.
I’m continuously improving my online security strategy so I may update this article periodically to add or remove items. I hope this article has exposed you to something new and I hope it encourages you to start improving your online security as well.